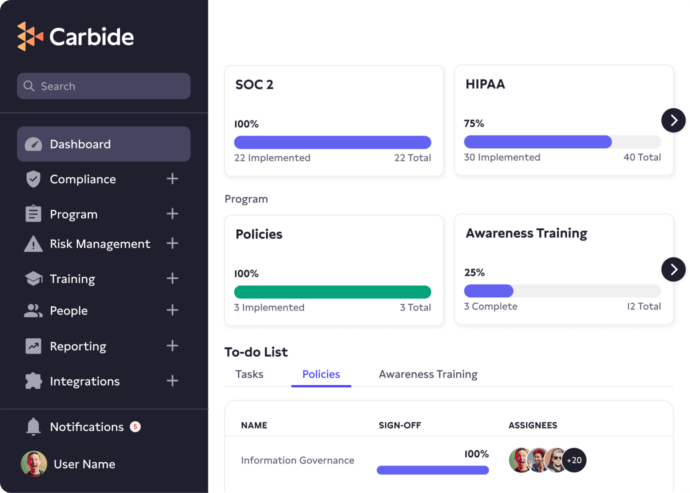
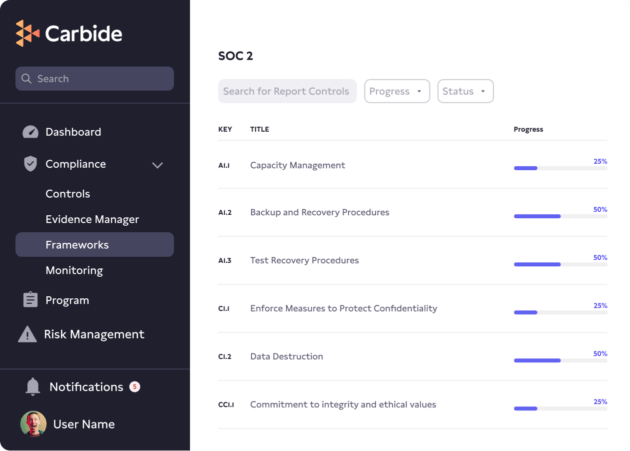
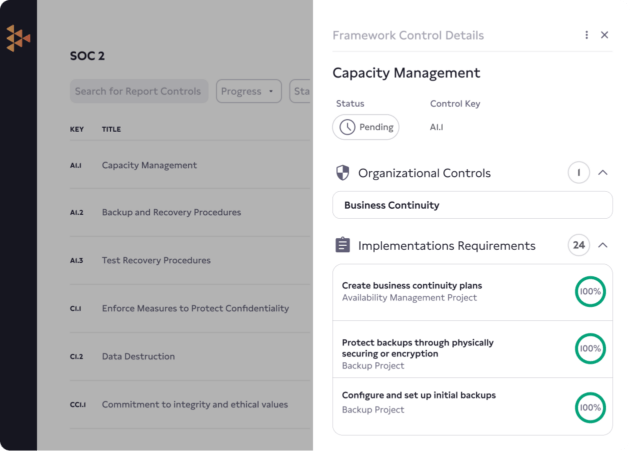
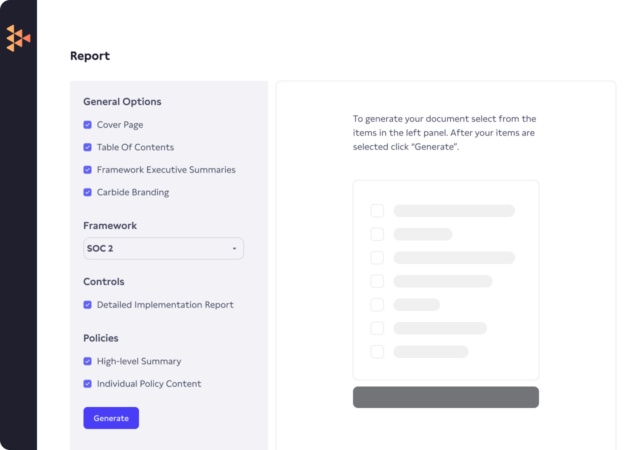
Achieving SOC 2 compliance shows your enterprise customers that you value security and have a strong security posture. The Service Organization Control 2 (SOC 2) audits are designed to validate a third-party vendor’s data management processes by checking the existence and effectiveness of data security, availability, processing integrity, confidentiality, and privacy controls at vendor organizations.
With the Carbide Platform and its embedded DRIVE approach (Design, Review, Implement, Validate, and Evolve) to information security, you can leave your checklists and spreadsheets in the past and follow our step-by-step plan to implement SOC 2 information security controls.